<MF2 VPN 구축 Test>
# Test 구성도

- R2 설정
interface Ethernet0/0
ip address 192.168.10.77 255.255.255.0
ip nat outside
ip virtual-reassembly in
!
interface Ethernet0/1
ip address 10.1.1.1 255.255.255.252
ip nat inside
ip virtual-reassembly in
--More-- !
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
no ip address
shutdown
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip nat inside source list 101 interface Ethernet0/0 overload
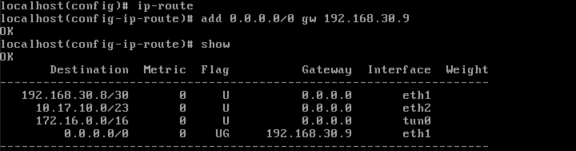
ip route 0.0.0.0 0.0.0.0 192.168.10.253
ip route 10.2.0.0 255.255.255.252 10.1.1.2
ip route 10.10.10.0 255.255.255.0 10.1.1.2
ip route 10.17.10.0 255.255.254.0 10.1.1.2
ip route 10.17.110.0 255.255.254.0 10.1.1.2
!
access-list 101 permit ip any any
2. BB 설정
interface Ethernet0/0
no switchport
ip address 10.1.1.2 255.255.255.252
duplex auto
!
interface Ethernet0/1
no switchport
ip address 10.10.10.1 255.255.255.0
2. BB 설정
interface Ethernet0/0
no switchport
ip address 10.1.1.2 255.255.255.252
duplex auto
!
interface Ethernet0/1
no switchport
ip address 10.10.10.1 255.255.255.0
duplex auto
!
interface Ethernet0/2
no switchport
ip address 10.2.1.1 255.255.255.252
duplex auto
!
interface Ethernet0/3
!
ip forward-protocol nd
!
no ip http server
--More-- no ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 10.1.1.1
ip route 10.17.10.0 255.255.254.0 10.2.1.2
ip route 10.17.110.0 255.255.254.0 10.2.1.2
3. R1 설정
interface Ethernet0/0
ip address 192.168.30.1 255.255.255.252
!
interface Ethernet0/1
ip address 192.168.30.9 255.255.255.252
!
interface Ethernet0/2
--More-- ip address 192.168.30.5 255.255.255.252
!
interface Ethernet0/3
ip address 192.168.10.78 255.255.255.0
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 192.168.10.80 255.255.255.255 192.168.10.253
4. FW 설정



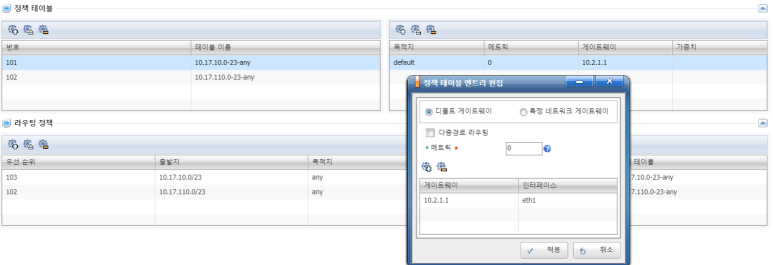
Source Routing 설정

지점(Branch) 등록

보안 정책 설정(FW, FW1, FW2 모두 동일하게 설정)

방화벽 정책 설정(IPSec 서비스객체를 허용해주기 위함)
5. FW2 설정


지점(Center)연결 설정
6. FW3 설정



지점(Center) 연결 설정
7. SW4, 5, 6 설정
## SW4 ##
interface Ethernet0/0
switchport access vlan 10
switchport mode access
!
interface Ethernet0/1
switchport access vlan 10
switchport mode access
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Vlan10
ip address 10.10.10.10 255.255.255.0
## SW5 ##
interface Ethernet0/0
switchport access vlan 110
switchport mode access
!
interface Ethernet0/1
switchport access vlan 110
switchport mode access
!
interface Ethernet0/2
!
interface Ethernet0/3
!
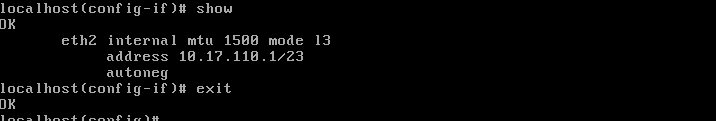
interface Vlan110
ip address 10.17.110.10 255.255.254.0
!
ip default-gateway 10.17.110.1
ip forward-protocol nd
## SW6 ##
interface Ethernet0/0
switchport access vlan 10
switchport mode access
!
interface Ethernet0/1
switchport access vlan 10
switchport mode access
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Vlan10
ip address 10.17.10.10 255.255.254.0
!
ip default-gateway 10.17.10.1
8. VPC 10, 11, 12 설정
## VPC 10 ##
VPCS> ip 10.10.10.100 /24 10.10.10.1
Checking for duplicate address...
VPCS : 10.10.10.100 255.255.255.0 gateway 10.10.10.1
VPCS> show
NAME IP/MASK GATEWAY GATEWAY
VPCS1 10.10.10.100/24 10.10.10.1
fe80::250:79ff:fe66:680a/64
VPCS> save
Saving startup configuration to startup.vpc
. done
## VPC 11 ##
VPCS> ip 10.17.110.100/23 10.17.110.1
Checking for duplicate address...
VPCS : 10.17.110.100 255.255.254.0 gateway 10.17.110.1
VPCS> save
Saving startup configuration to startup.vpc
. done
## VPC 12 ##
VPCS> ip 10.17.10.100/23 10.17.10.1
Checking for duplicate address...
VPCS : 10.17.10.100 255.255.254.0 gateway 10.17.10.1
VPCS> save
Saving startup configuration to startup.vpc
. done

VPN 상태 확인

각 VPC 간에 VPN 통신 확인
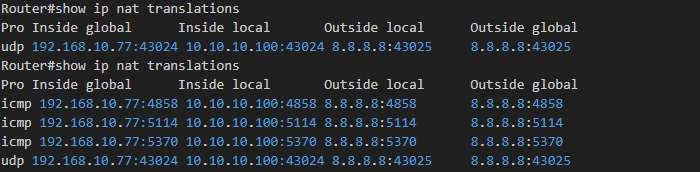
VPC에서 인터넷 통신시 NAT 로그 확인